Navigation
Navigation
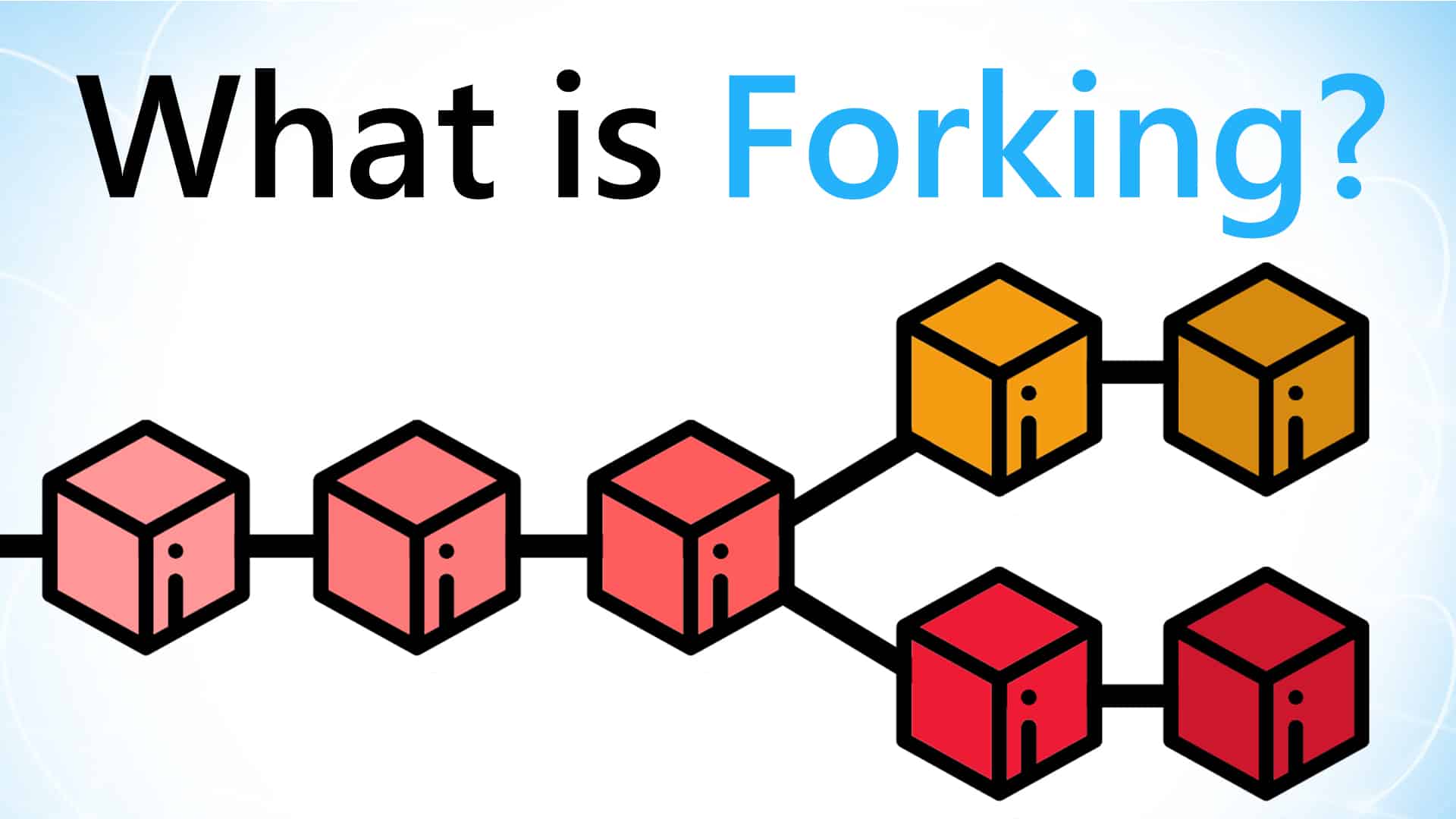
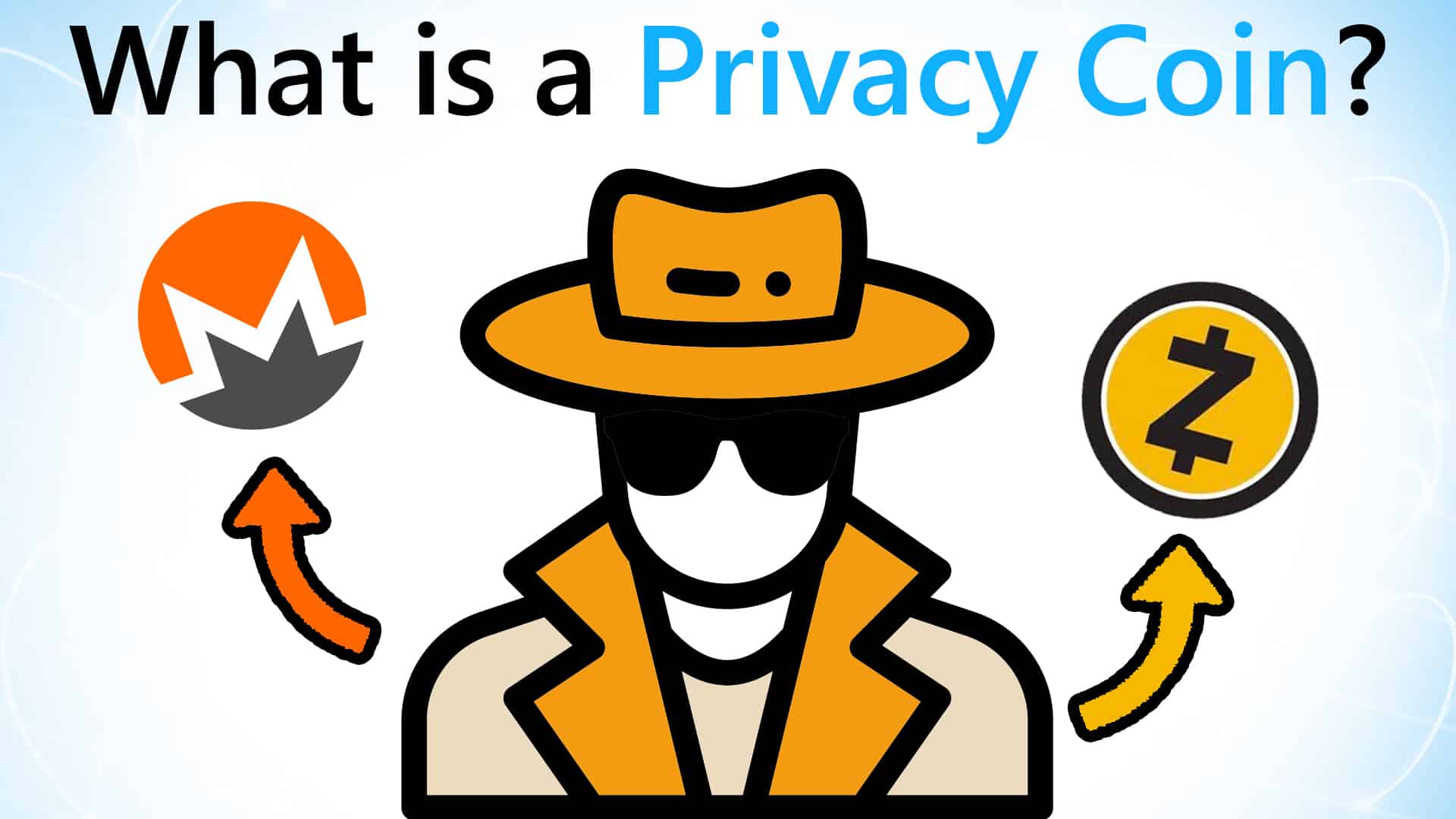
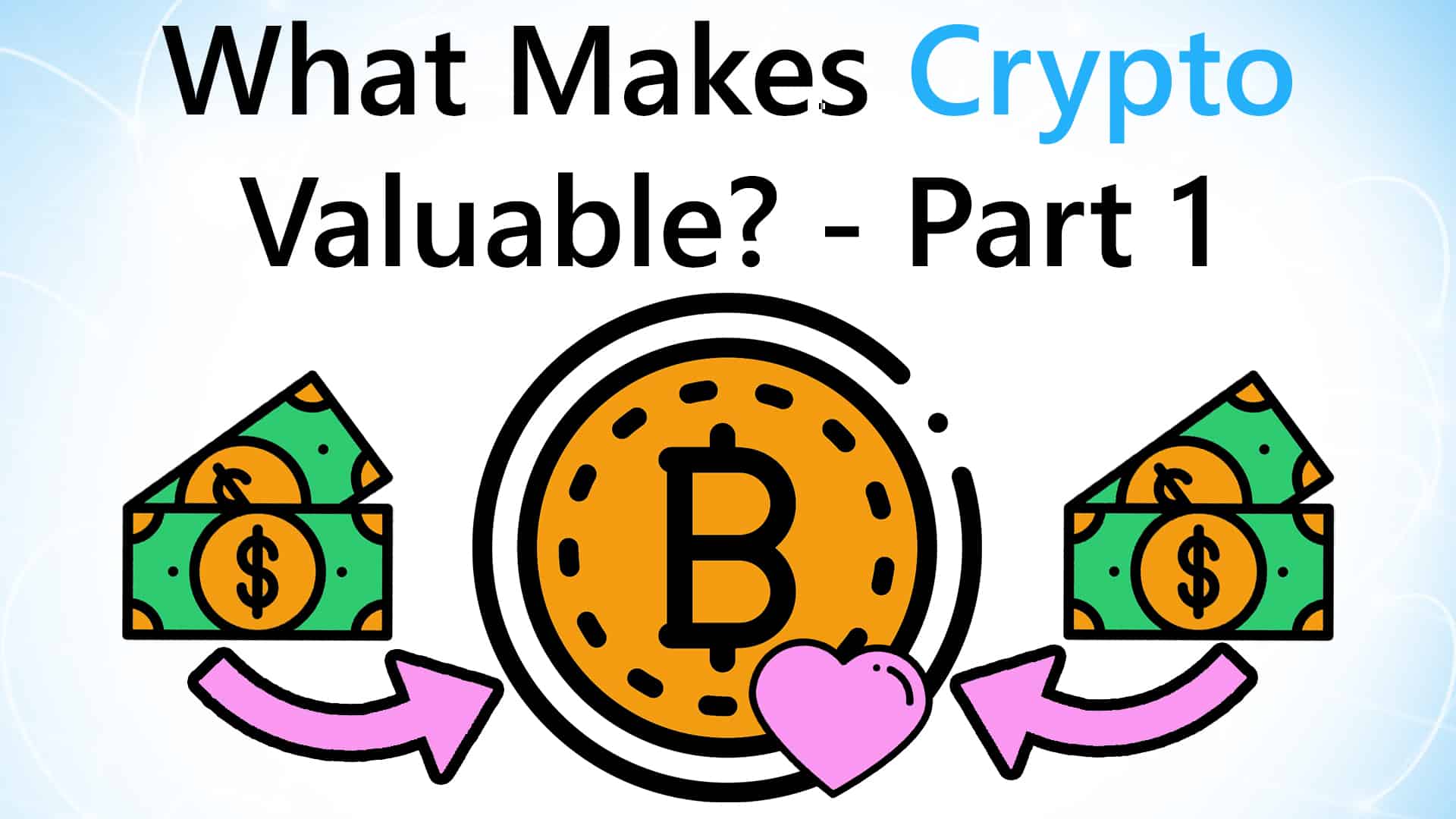
Video Guide: What is Decred
Like what you have watched? Give us one like or share it to your friends
70
Hungry for knowledge?
New guides and courses each week
Looking to invest?
Market data, analysis, and reports
Just curious?
A community of blockchain experts to help
Get started today
Already have an account? Sign In