Contents
What are Smart Contracts?
A smart contract is a self-executing digital agreement that enables two or more parties to exchange money, property, shares, or anything of value in a transparent, conflict-free way while avoiding the need for a third party.
To lay it out in the most simplest way, you can compare smart contracts to a vending machine for complex transactions.
Smart contracts work by following simple “if/when…then…” statements that are written into code on a blockchain. A network of computers executes the actions when predetermined conditions have been met and verified. These actions could include releasing funds to the appropriate parties, registering a vehicle, sending notifications, or issuing a ticket. The blockchain is then updated when the transaction is completed. That means the transaction cannot be changed, and only parties who have been granted permission can see the results.
With smart contracts, you simply drop a bitcoin into the vending machine (i.e. ledger), and your escrow, deed, contract, goods, driver’s licence, or whatever the contract is for, simply drops into your account.
The smart contract does all the work to determine whether the conditions of the order were satisfied.
Smart contracts both define the rules and penalties around an agreement in the same way that a traditional contract does, and also automatically enforces those obligations.
OK, so where do smart contracts exist? Where are they executed? And how do they work?
WHAT YOU NEED TO KNOW
- Smart contracts are self-executing lines of code with the terms of an agreement between buyer and seller automatically verified and executed via a computer network.
- Nick Szabo, an American computer scientist who invented a virtual currency called “Bit Gold” in 1998,1 defined smart contracts as computerized transaction protocols that execute terms of a contract.2
- Smart contracts deployed to blockchains render transactions traceable, transparent, and irreversible.
Contents
Benefits of Smart Contracts
Accuracy, Speed, and Efficiency
- The contract is immediately executed when a condition is met.
- Because smart contracts are digital and automated, there is no paperwork to deal with, and
- No time was spent correcting errors that can occur when filling out documentation by hand.
Trust and Transparency
- There’s no need to worry about information being tampered with for personal gain because there’s no third party engaged and
- Encrypted transaction logs are exchanged among participants
Smart contracts are verified, executed, and enforced by a computer program that runs on a blockchain network. When both parties involved in the smart contract agree to its terms, the program will automatically execute. This eliminates the need for a third party, as the contract is verified and enforced by the blockchain network.
Because smart contracts are executed by code rather than people, they remove the possibility of human error and can automate many tasks that would traditionally require human interaction.
One of the best things about the blockchain is that, because it is a decentralized system that exists between all permitted parties, there’s no need to pay intermediaries (middlemen) and it saves you time and conflict.
Sure, Blockchains have their problems, but they are undeniably faster, cheaper, and more secure than traditional systems. This is why we’re seeing more smart contracts being executed on different blockchain networks including Ethereum, Solana, Tezos, Hyperledger, etc.
Vitalik Buterin on Smart Contracts
Identifying Real-life Use Cases of Smart Contracts
Smart Contracts Are Not Perfect
Create Your Own Smart Contract!
Unfolding the Future of Smart Contracts
Vitalik Buterin on Smart Contracts
As Vitalik Buterin, the 28-year-old founder of ethereum, explained it at a DC Blockchain Summit, “In a smart contract approach, an asset or currency is transferred into a program and the program runs this code and at some point it automatically validates a condition and it automatically determines whether the asset should go to one person or back to the other person, or whether it should be immediately refunded to the person who sent it or some combination thereof.”
In the meantime, the decentralized ledger also stores and replicates the document which gives it a certain security and immutability.
Example: Escrow for Transactions
Suppose you rent an apartment from me.
You can do this through the blockchain by paying in cryptocurrency. You get a receipt which is held in our virtual contract; I give you the digital entry key which comes to you by a specified date. If the key doesn’t come on time, the blockchain releases a refund.
If I send the key before the rental date, the function holds it, releasing both the fee and key to you and me respectively when the date arrives.
The system works on the If-Then premise and is witnessed by hundreds of people, so you can expect a faultless delivery.
If I give you the key, I’m sure to be paid. If you send a certain amount in bitcoins, you receive the key. The document is automatically canceled after the allotted time, and the code cannot be interfered with by either of us without the other knowing, since all participants are simultaneously alerted.
You can use smart contracts for all sorts of situations ranging from:
- financial derivatives
- insurance premiums
- breach contracts
- property law
- credit enforcement
- financial services
- legal processes
- crowdfunding agreements.
Identifying Real-life Use Cases of Smart Contracts
Jerry Cuomo, vice president for blockchain technologies at IBM, believes smart contracts can be used all across the chain, from financial services, to healthcare, to insurance. Here are some examples.
DeFi Applications

A major change in how we manage money is underway as we see DeFi Apps growing into the mainstream.
Decentralized finance is an exit from traditional banking services and norms. This is a highly delicate transition but one that appears to be inevitable.
We have the numbers to prove it:
The annual transaction value of DeFi grew by 14x in 2020 and more than quadrupled to $112.07 billion in 2021 with over USD $20 billion in total value locked up in DeFi smart contracts alone.
Smart contracts in DeFi are facilitating the exchange of goods, services, data, funds and so on. Users of centralized financial institutions, such as banks and credit unions, rely on intermediaries to execute a transaction. Whereas, DApps are using smart contracts to ensure that each action is genuine, transparent, and free of human error.
NFTs
In just a couple of years, NFTs have exploded in the market, with the Market cap closing in at a whopping $40.9 billion in 2021 as they turned out to be the most successful use-case of smart contracts.
NFTs are created through a minting process that requires smart contracts deployed on the blockchain.
A smart contract is a tool that allows implementing a sale agreement between the NFT owner and the buyer. The smart contract contains information on the NFT, such as the work’s creator, other parties who are entitled to royalties each time the NFT is sold, and the work’s ownership history.
The majority of NFTs are not recorded on the blockchain since keeping so much data on the blockchain is both costly and energy intensive. As a result, smart contracts frequently include a link to the work they represent, which can be viewed by only the owner.
Government
Insiders vouch that it is extremely hard for our voting system to be rigged, but nonetheless, smart contracts would allay all concerns by providing an infinitely more secure system. Ledger-protected votes would need to be decoded and require excessive computing power to access. No one has that much computing power, so it would need God to hack the system!
Secondly, smart contracts could hike low voter turnout. Much of the inertia comes from a fumbling system that includes lining up, showing your identity, and completing forms. With smart contracts, volunteers can transfer voting online and millennials will turn out en masse to vote for their POTUS.
Case History
For the 2020 US Presidential Elections, the Utah County successfully managed to collect votes from absentee voters through a blockchain-powered mobile application called Voatz. The voter identity is kept hidden behind a unique signature/hash-value, and the relevant data also remains secure within the blockchain free of external threats.
Management
The blockchain not only provides a single ledger as a source of trust, but also shaves off possible snags in communication and workflow because of its accuracy, transparency, and automated system.
Ordinarily, business operations have to endure a back-and-forth, while waiting for approvals and for internal or external issues to sort themselves out. A blockchain ledger streamlines this. It also cuts out discrepancies that typically occur with independent processing and that may lead to costly lawsuits and settlement delays.
Case History
In 2015, the Depository Trust & Clearing Corp. (DTCC) used a blockchain ledger to process more than $1.5 quadrillion worth of securities, representing 345 million transactions.
Supply Chain
Smart contracts work on the If-Then premise so, to put in Jeff Garzik’s words,
“UPS can execute contracts that say, ‘If I receive cash on delivery at this location in a developing, emerging market, then this other [product], many, many links up the supply chain, will trigger a supplier creating a new item since the existing item was just delivered in that developing market.’”
All too often, supply chains are hampered by paper-based systems, where forms have to pass through numerous channels for approval, which increases exposure to loss and fraud. The blockchain nullifies this by providing a secure, accessible digital version to all parties on the chain and automates tasks and payment.
Case History
Barclays Corporate Bank uses smart contracts to log a change of ownership and automatically transfer payments to other financial institutions upon arrival
Automobile
There’s no doubt that we’re progressing from slothful pre-human vertebrates to super-smart robots. Think of a future where everything is automated. Google’s getting there with smartphones, smart glasses, and even smart cars. That’s where smart contracts help.
One example is the self-autonomous or self-parking vehicles, where smart contracts could put into play a sort of ‘oracle’ that could detect who was at fault in a crash; the sensor or the driver, as well as countless other variables. Using smart contracts, an automobile insurance company could charge rates differently based on where, and under which, conditions customers are operating their vehicles.
Real Estate
If you wanted to rent your apartment to someone, you’d need to pay a middleman such as Craigslist or a newspaper to advertise, and then again you’d need to pay someone to confirm that the person paid rent and followed through.
A decentralized solution can help cut your costs. All you do is pay via cryptocurrency and encode your contract on a smart contract. Everyone sees, and you accomplish automatic fulfillment. Brokers, real estate agents, hard money lenders, and anyone associated with the property game can profit.
Smart contracts are revolutionary in terms of transforming the current real estate practices.
Smart contracts are replacing traditional contracts as the sole agreement between the seller and buyer. It automatically executes the requirements as soon as specific conditions of the contract are met.
Smart contracts guarantee trust through a single version of the truth by establishing trust. All the parties including the bank, the agent, and the mortgage lender can sign an agreement via smart contracts. Because transactions are kept on a blockchain, this shared ledger enables the parties involved to look over the process at any moment and from anywhere.
Healthcare

Personal health records could be encoded and stored on the blockchain with a private key which would grant access only to specific individuals. The same strategy could be used to ensure that research is conducted via HIPAA laws (in a secure and confidential way).
Receipts of surgeries could be stored on a blockchain and automatically sent to insurance providers as proof-of-delivery. The ledger, too, could be used for general healthcare management, such as supervising drugs, regulation compliance, testing results, and managing healthcare supplies.
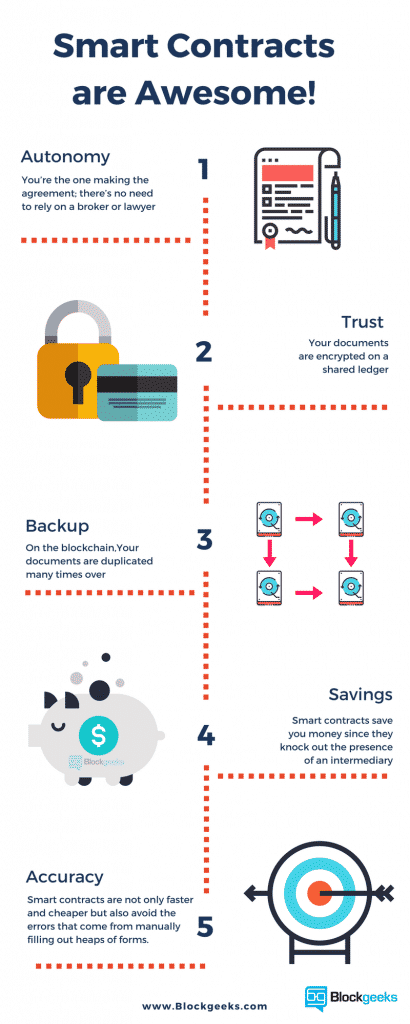
Smart Contracts are Awesome!
Here’s what smart contracts give you:
Autonomy
You’re the one making the agreement; there’s no need to rely on a broker, lawyer, or other intermediaries to confirm. Incidentally, this also knocks out the danger of manipulation by a third party, since execution is managed automatically by the network, rather than by one or more, possibly biased, individuals who may err.
Trust
Your documents are encrypted on a shared ledger. There’s no way that someone can say they lost it.
Backup
Imagine if your bank lost your savings account. On the blockchain, each and every one of your friends have your back. Your documents are duplicated many times over.
Safety
Cryptography, the encryption of websites, keeps your documents safe. There is no hacking. In fact, it would take an abnormally smart hacker to crack the code and infiltrate.
Smart contracts offer security of a blockchain network. The technology itself is capable of providing the right kind of security to prevent potential hack, however, writing a smart contract also equally accounts for ensuring its safety.
Much like what happened with The DAO hack in 2016, a mere loophole in a smart contract resulted in the biggest heist of the crypto market. Had that loophole been addressed earlier, it could have been prevented. But here’s the catch, because you can track every movement on a blockchain, the minute the stolen ether/ETH enters circulation, those behind the heist will be exposed. So all that stolen crypto is as good as nothing.
A simple human-error in writing a smart contract compromised its safety. To prevent that, you will need the right developers who could write a fool-proof smart contract.
Speed
You’d ordinarily have to spend chunks of time and paperwork to manually process documents. Smart contracts use software code to automate tasks, thereby shaving hours off a range of business processes.
Savings
Smart contracts save you money since they knock out the presence of an intermediary. You would, for instance, have to pay a notary to witness your transaction.
Accuracy
Automated contracts are not only faster and cheaper but also avoid the errors that come from manually filling out heaps of forms.
Smart Contracts Are Not Perfect
Smart contracts are far from perfect. What if bugs get in the code? Or how should governments regulate such contracts? Or, how would governments tax these smart contract transactions? As a case in point, remember the example quoted earlier about my rental situation?
What happens if I send the wrong code, or, as lawyer Bill Marino points out, I send the right code, but my apartment is condemned (i.e., taken for public use without my consent) before the rental date arrives? If this were the traditional contract, I could rescind it in court, but the blockchain is a different situation. The contract performs, no matter what.
The list of challenges goes on and on. Experts are trying to unravel them, but these critical issues do dissuade potential adopters from signing on.
Here are a few quick takeaways to dwell on what problems you could face with Smart Contracts:
- Smart contracts are not reversible, meaning that if there is a problem with the contract, it can be difficult or impossible to fix.
- Smart contracts may not always be reliable, as they are executed on a blockchain network. This means that they theoretically can be subject to downtime and outages, although Ethereum has proven incredibly reliable, newer smart contract networks like Solana have experienced a few outages as the technology is still very much in development
- Smart contracts can be costly to develop and require a high level of technical expertise.
- Smart contracts are not always customizable, meaning that they may not be suitable for all businesses or transactions.
Create Your Own Smart Contract!
In order to create a smart contract, you will need to have a basic understanding of blockchain technology and how smart contracts work. You will also need to have a working knowledge of the programming language that is used to write smart contracts, which is typically Solidity.
Once you have acquired this knowledge, you can then begin to create your own smart contracts. There are a number of blockchain networks that allow you to create and deploy smart contracts.
One of the most popular platforms is Ethereum.
Ethereum is a public blockchain platform that allows you to create and execute smart contracts.
The process of creating a smart contract on Ethereum is relatively simple. You will first need to create a new account on the Ethereum network. Once you have created an account, you can then begin to create smart contracts. The process of creating a smart contract is as follows:
- Create a new contract file
- Write the smart contract code in Solidity
- Deploy the smart contract to the Ethereum network
Once you have deployed your smart contract, it will be stored on the Ethereum blockchain and will be executed by the Ethereum network.
Unfolding the Future of Smart Contracts
Part of the future of smart contracts lies in entangling the issues we discussed earlier.
In Cornell Tech, for instance, lawyers, who insist that smart contracts will enter our everyday life, have dedicated themselves to researching these concerns.
Especially as the NFT Marketplaces have sprung up, there’s more at stake now than ever to solve the problematic aspects of smart contracts.
Smart contracts may impact changes in certain industries, especially law. This is because lawyers will transfer from writing traditional contracts to producing standardized smart contract templates, similar to the standardized traditional contracts that you’ll find on LegalZoom.
Merchant acquirers, credit companies, and accountants may also employ smart contracts for tasks, such as real-time auditing and risk assessments.
As we see more DeFi Apps being deployed around the world and NFT markets multiply in value, it’s evident that Smart contracts are merging into a hybrid of paper and digital content where contracts are verified via blockchain and substantiated by physical copy.
Smart contracts will only continue to improve, and as the technology evolves, they will be increasingly trusted and efficient.
We, at Blockgeeks, offer detailed courses on Blockchain technology including Ethereum Development covering all the important topics you need to get started with Smart Contracts!
| Explore Blockchain Courses! |
|---|





![What is Ethereum? [The Most Updated Step-by-Step-Guide!]](https://blockgeeks.com/wp-content/uploads/2016/10/whatiseth.jpg)
Thanks for the article! I was searching for a perfect guide to know about Ethereum and came across this. I hope most of the future Ethereum Tokens can provide a good amount of funds! You can know more about Ethereum here!
Great article
very usefull block!
Hi, I am an engineering student from South Korea. I’ve found this article very helpful, understanding smart contract. Can I translate this article in Korean for a blog post? I’ll link this url, of course.
A “smart” contract is a legal contract. It is just in a different form. An oral agreement is (apart from some special instances) a contract. There is no need for it to be in writing. And, with the invention of the telephone, a contract could be made by phone! And later by email! The process that you outline has all the ingredients of a typical contract, though formed by a different medium. There will still be, somewhere, written terms and conditions, though these terms and conditions may be reduced to code, but maybe not. The legal principles of forming a contract are all there – and need to be for the agreement to be legally-enforceable. (And a “smart” contract is not at all smart). Excellent article, by the way.
great block
Hello Sir, Your Article is really a gold for starters, I am a Beginner working on Smart contract but have some question which is continuously roaming in my mind question are
1. How smart contracts takes inputs from external world?
2. How should systems know the certain conditions are fulfilled in smart contracts?
3. How real-world business expectation work on Smart Contract?
if you blockchained the world you can do it easy
This is clearly the future of every aspect of our lives. Being the first mover in this aspect of blockchain technology it is my view that Ethereum will continue to be the trend-setter and the platform to go to for institutions, governments and corporations adopting blockchain technology for efficiency, utility, security, due diligence capabilities, etc.
At around $300 a coin (19 October 2017) Ethereum is massively undervalued.
Time will tell but from this end the revolutionary and massive disruptive nature of Ethereum is as clear as crystal.
I think the smart contract just like any new form of technology that needs to iron out the bugs.
Start testing those scenarios first, and then let the brainstorming begin. I’m sure we had
all kinds of questions and legal issues about the horse and buggy moving into the automobile era…and yet here we are.
We can start testing with small dollar transactions and move from there.
Great article!
Another good guide on smart contracts: https://coincenter.org/entry/what-are-smart-contracts-and-what-can-we-do-with-them
Thank you Dmitry
What are the biggest challenges and limitations of smart contracts as of today?
Today, the biggest challenge is the misconception of what the term “smart contract” really means, as it is not a contract in the conventional sense of the word – so the term can be misleading. However, once that gets cleared up, there are many other limitations that will need to be addressed, such as how do you trust them to do what they promise to do, and what recourse do you have if they don’t?
I would say it’s more like a individual deal and agreement. Contract is more of legal enforcement
To be or not to be? Code is Law or Code is not Law ?
Just think what happened to TheDAO. To be part of the DAO people accepted “terms and conditions” in English while services in the platform run pieces of Ethereum code. Obviously “terms and conditions” cannot include BUGS and cannot provide a perfect match between english and solidity code (for instance)
So we have 3 big challenges :
1) build a bridge between smart contracts and paper contracts.
Common Accord is a very promising project aimed at this goal
http://www.commonaccord.org/
http://blogchaincafe.com/common-accord-le-pont-smart-contracts-contrats-papier
2) produce a 100% bug-free code for smart contracts
3) find a way to update smart contracts to take into account evolutions in laws
Maybe a fourth one:
4) find a way to hide public information for some kind of smart contracts that need privacy (using z-Cash+Ethereum, for instance)
Excellent Summary! Though i wonder if we would every have bug-free smart contracts…big challenge, in any software development.
Dmitry Buterin Bug free. no. But my thoughts are. What about A.I and Smart contracts, Hmmmm???? 🙂
‘Smart Contracts’ are to ‘Legal Contracts’ what ‘AI’ is to ‘Expert Systems’. Worlds of differences.
Take a peek at the ‘Four Corners Rule’ and the ‘Parol Evidence Rule’ for legal contracts.
It’s a great view. We are a law firm in Vietnam and looking forward to making something similar. Wondering if we can have a community to contribute to this such an Open Source project
I see three main limitations of autonomous contracts :
– Private keys management
– Identity management
– Good practices and security
That’s ok, we take these challenges!
https://twitter.com/julienbrg
jbrg Out of those three: Which one do you think we should tackle first?