Contents
|
|
RSK (a.k.a Rootstock) is one of the most critical components in the Bitcoin ecosystem that brings in smart contract functionality to the protocol. RSK is connected to the Bitcoin blockchain via sidechain technology. As such, RSK enables developers to create applications compatible with Ethereum (the web3/EVM/Solidity model) while still enjoying the Bitcoin blockchain’s security. The core features of RSK are as follows:
- It’s a Turing-complete resource-accounted deterministic virtual machine (for smart contracts) is compatible with the Ethereum Virtual Machine (EVM).
- A SHA256D merge-mining consensus protocol (for consensus security relying on Bitcoin’s miners) with a 30-second block interval. (for fast payments).
- A two-way pegged Bitcoin sidechain (for BTC denominated trade) based on a Powpeg.
Let’s expand on the last point.
Contents
RSK Powpeg – An Introduction
RSK’s 2-way peg is called the “Powpeg.” The new and updated Powpeg protects private keys stored in special-purpose PowHSMs based on tamper-proof secure elements (SE). PowHSM is an external tamper-proof device that creates and protects one of the private keys required for Bitcoin’s multi-signature protocol. This ensures that the individual signatures can only be controlled by cumulative chain proof-of-work.
RSK Powpeg Ecosystem
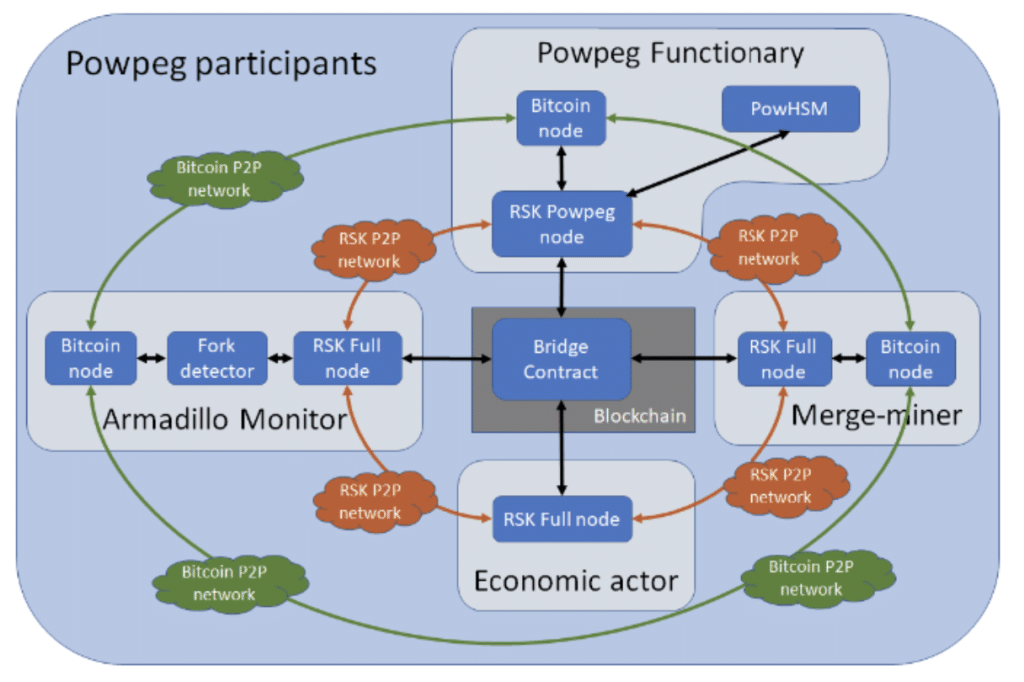
#1 Powpeg Pegnatories
The first participant that we will be looking into is pegnatories.. Their roles are as follows:
- Run a Powpeg node, which is a special type of full node
- To ensure that the PowHSM is connected with the Powpeg node to sign peg-out transactions.
- They are not actively involved in the actual process of signing transactions.
- They don’t participate in block production on the RSK blockchain.
Each pegnatory maintains a PowHSM which is connected to a special type of RSK full node called “Powpeg Node.” A Powpeg node has two special features:
- They are designed to have maximal connectivity.
- They communicate information about the RSK blockchain to the PowHSM. Chief among them being cumulative work.
#2 Merge-miners and the Armadillo Monitor
RSK maintains its consensus through merge mining. As such, merge miners form the backbone of the entire protocol. Since a huge portion of miners participates in RSK, it has the persistence and liveness properties required to secure the overall network. The role of the merge miners are as follows:
- They are the most extensive and crucial layer of RSK’s defense-in-depth approach to secure the bridge between RSK and Bitcoin.
- The pegnatories rely on merge-mining stability to ensure valid multi-signature transactions are signed and validated in a secure and timely manner.
What is Armadillo?
Armadillo is a suite of tools that helps protect the RSK blockchain from malicious merge-mining attacks. Armadillo is part of RSK’s defense-in-depth approach, which provides users of the 2-way peg secondary protection if the merge-mining hashrate fails or the RSK network is attacked.
The Armadillo monitor ensures the following:
- It proactively makes sure that the merge-mining algorithms used in RSK and Bitcoin are working as expected.
- It tracks all parallel RSK forks by inspecting Bitcoin merge-mining tags. If large conflicting forks are detected, Armadillo automatically sends alerts to economic actors like exchanges and functionary nodes.
#3 Economic Actors and the Bridge Contract
Economic Actors are a critical component of the entire RSK ecosystem. These actors include merchants and exchanges that interact with the 2-way peg by sending and receiving peg-in and peg-out transactions to the Bridge smart contract through the RSK network.
The Bridge is a precompiled smart contract living in the RSK blockchain. Its features are as follows:
- The Bridge’s primary role is to maintain an updated view of the Bitcoin blockchain, verify peg-in requests, and command peg-outs.
- The Bridge contracts manage a Bitcoin wallet in the SPV (Simple Payment Verification) mode. In this mode, the transactions are confirmed by block headers. The block headers are minimally validated, but these validations still include the expected amount of proof-of-work (POW).
- The Bridge waits for 100 confirmations before confirming a peg-in transaction. This is done to prevent invalid forks.
How RSK Powpeg ensures security
Bitcoiners prefer security over everything else. This is why RSK’s Powpeg needs to offer a more holistic, real-world security that can be analyzed for different points of view – technical, operational, and reputational. So, let’s go through the different security measures that RSK has taken.
#1 Defense-in-Depth
Defense-in-depth is an all-encompassing term that defines the careful separation of responsibilities. This makes sure that compromising the system will require the malicious parties to neutralize multiple elements. Here are some points to keep in mind about defense-in-depth:
- Malicious miners, pegnatories, PowHSM manufacturer, developers won’t be able to steal the funds of the peg on their own
- Consensus roles hardcoded in the software firmware governs the peg process.
- RSK community protects the code from mistakes
- The community’s goal is to improve the Powpeg by adding more protective layers. Each layer adds more security.
Cheating the PowHSM becomes nearly impossible without hacking several Bitcoin mining pools due to its defense-in-depth strategy. This is similar to a “vetocracy” system wherein no single entity can acquire enough power to override decisions and make monumental changes (more on this in a bit).
#2 Coordination Transparency
- All communications between pegnatories occur over the RSK chain. Malicious pegnatories can’t communicate with each other on-chain secretly. Plus, there are no pre-established subsystems that allow them to do so.
- All the messages exchanged between the pegnatories on-chain are public.
- The public nature of the chain forces the PowHSM to be transparent and allows network participants to track the PowHSM internal state periodically.
- Powpeg pegnatories could connect to the network over Tor or change their IPs daily to obfuscate themselves from external hackers.
- The bridge smart contract builds the peg-out transaction and doesn’t let any of the PowHSMs pick anything related to the transaction to sign.
- RSK consensus decides the whole transaction content.
#3 Firmware Attestation
To ensure that all the system’s actions are predictable, RSK PowHSM firmware and the full node and Powpeg nodes are all generated using deterministic builds. However, the current version of the PowHSM firmware isn’t entirely trustless. An auditing group needs to attest to the correctness of the firmware installation on each new device or batch of devices.
However, this will change with PowHSM firmware version 2.1, which will provide firmware attestation using the device’s security features. To achieve trustlessness, PowHSM will include firmware attestation as part of their deployment procedures, or even periodically as keep-alive messages. Eventually, attestation messages will be stored in the blockchain, and every member of the community will be able to validate PowHSM firmware.
#4 Proof of Work = Proof of Time
RSK receives a large portion of Bitcoin’s hashrate through merge-mining. This ensures that the amount of cumulative work required by the PowHSM acts as a rate limiter for any attack.
In simple terms, if a malicious actor somehow manages to cheat the PowHSM into confirming a malicious fork, it implies that a large-scale pool has been acting against the protocol’s interest for multiple days. An attack of this magnitude would be transparent and visible to both the Bitcoin and RSK communities, which should give them enough time to respond, in kind, to the attackers.
#5 Peg-in and Peg-out Finality
Finality is vital for peg-in and peg-out transactions since the Bitcoin blockchain and RSK side chain aren’t entangled in a single chain. As such, the transfer of BTC between them must be considered final. If this isn’t done, it would be impossible to unlock bitcoins sent to one side from another safely. The only way that they can finalize the transactions is by a high number of block confirmations.
- Peg-in transactions: 100 Bitcoin blocks or 2000 RSK blocks
- Peg-out transactions: 4000 RSK blocks or 200 Bitcoin blocks.
Transactions signed by the federation nodes are considered final by the RSK and are broadcasted to the Bitcoin blockchain for inclusion. In the event of a malicious fork, the Powpeg nodes halt future peg-outs to prevent double-spending.
#5 Decentralization through vetocracy
We have touched on vetocracy before but it is the core philosophy behind RSK’s decentralization. In the context of blockchain technologies, a vetocracy means that a miner or group of miners becomes powerful enough to surpass 51% of the network’s overall hashrate. When they do so, they can take over the overall protocol. This is called a 51% attack.
So, how does RSK mitigate this issue? Let’s take a look.
- RSK has a large portion of the Bitcoin merge-mined hashrate which surpasses 51%. This means that a new group of merge-miners can’t hijack the protocol and force the PowHSMs to perform a malicious peg-out.
- Another security layer that the merge-miners are currently contemplating in their Powpeg2 (Powpeg squared) update is a second federation. Members of the second federation are automatically chosen on past merge-mining hashrate contributions by the Bridge contract.
- In the miner’s federation, each miner is expected to sign the peg-out transaction. In this scenario, every miner signature contributes with a specific score based on their corresponding hashrate and the acceptance threshold set as a minimum cumulative score. This implementation decentralizes the security of the funds of the peg and protects against a 51% attack.
- The ultimate goal for RSK is to build a drive chain. The Bitcoin scripts used by the RSK pegs are designed for easy compatibility with the drive chain BIP.
Is the Powerpeg censorship resistance?
Selective censorship in RSK is impossible since banning a transaction leads to a complete halt of the Powpeg. How does it work? Let’s see:
- If one Powpeg functionary attempts to censor one specific transaction, the other pegnatories sign and execute the peg-out transaction, causing the censorship attempt to fail.
- However, what if all the pegnatories turn Byzantine? In that case, the pegnatories cannot continue to perform other peg-outs as peg-outs are linked to UTXOs and the pegnatories can’t choose UTXOs for the peg-out transactions. These peg-out UTXOs are selected by the Bridge contract, forming a consensus-enforced chain.
Now, let’s take things to the extreme. What if a single government decides to shut down the Powpeg completely? This can be nearly impossible to do since the pegnatories are distributed all over the world. A shutdown attempt will only make RSK stronger as it will prompt the users to run their PowHSM device and a Powpeg node over Tor.
Plus, to prevent powerful government agencies from taking control of the protocol, RSK plans to add an emergency recovery multisig time-lock to activate one year after the Powpeg is proven dismantled.
Conclusion
As the RSK peg grows over time, more bitcoins are being moved into the sidechain. Compared to alternatives, the Powpeg combines strong security based on layered protections with maximum decentralization within the Bitcoin scripting system’s constraints. As Bitcoiners value security over the latest over-hyped functionality, RSK is bound to become the first choice of DeFi for Bitcoiners. The peg’s security and decentralization will continue to increase, not only technically but also in quality and quantity, and with more and better pegnatories participating.