 Navigation
Navigation
What is Hashing & Digital Signature in The Blockchain?
|
|
Hi, everyone. Today, we’re going to be talking about the word blockchain and breaking it down to understand what does it mean when someone says, “Blockchain.” We’re going to take the time to understand the cryptography behind the blockchain technology. There are two main cryptographic concepts that underpin blockchain technology. The first is hashing, and the second is digital signatures.
What is Hashing & Digital Signature in The Blockchain?
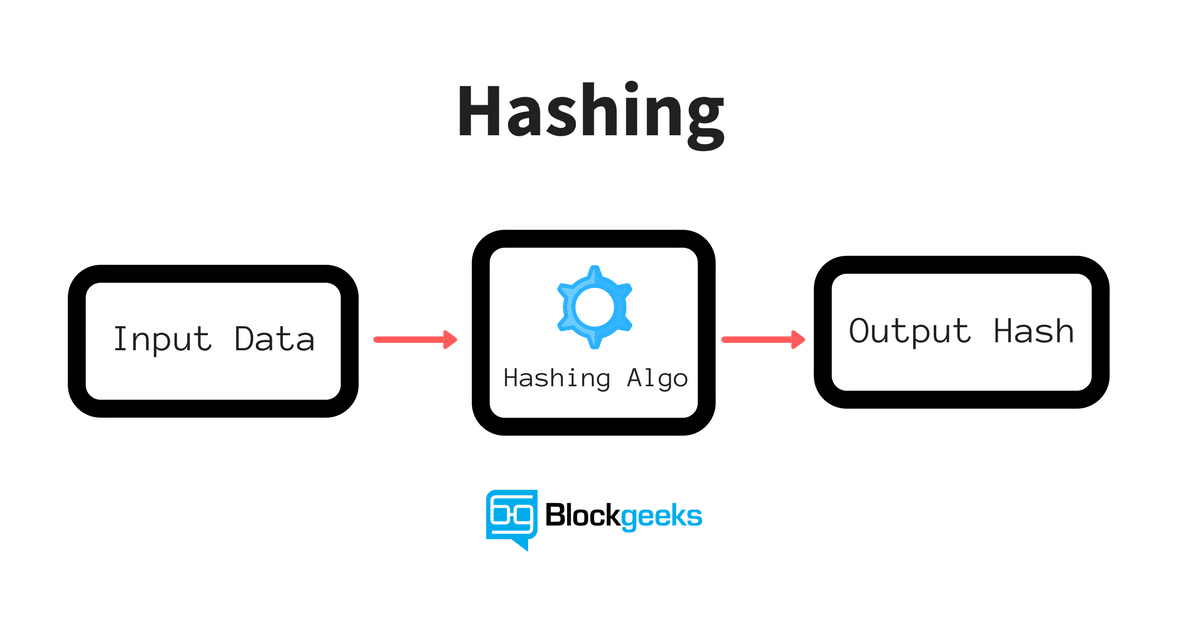
Hashing refers to the concept of taking an arbitrary amount of input data, applying some algorithm to it, and generating a fixed-size output data called the hash. The input can be any number of bits that could represent a single character, an MP3 file, an entire novel, a spreadsheet of your banking history, or even the entire Internet. The point is that the input can be infinitely big. The hashing algorithm can be chosen depending on your needs and there are many publicly available hashing algorithms. The point is that the algorithm takes the infinite input of bits, applies some calculations to them, and outputs a finite number of bits. For example, 256 bits.
What can this hash be used for? A common usage for hashes today is to fingerprint files, also known as check zones. This means that a hash is used to verify that a file has not been tampered with or modified in any way not intended by the author. If WikiLeaks, for example, publishes a set of files along with their MD5 hashes, whoever downloads those files can verify that they are actually from WikiLeaks by calculating the MD5 hash of the downloaded files, and if the hash doesn’t match what was published by WikiLeaks, then you know that the file has been modified in some way.
How does the blockchain make use of hashes? Hashes are used in blockchains to represent the current state of the world. The input is the entire state of the blockchain, meaning all the transactions that have taken place so far and the resulting output hash represents the current state of the blockchain. The hash is used to agree between all parties that the world state is one in the same, but how are these hashes actually calculated?
The first hash is calculated for the first block or the Genesis block using the transactions inside that block. The sequence of initial transactions is used to calculate a block hash for the Genesis block. For every new block that is generated afterward, the previous block’s hash is also used, as well as its own transactions, as input to determine its block hash. This is how a chain of blocks is formed, each new block hash pointing to the block hash that came before it. This system of hashing guarantees that no transaction in the history can be tampered with because if any single part of the transaction changes, so does the hash of the block to which it belongs, and any following blocks’ hashes as a result. It would be fairly easy to catch any tampering as a result because you can just compare the hashes. This is cool because everyone on the blockchain only needs to agree on 256 bits to represent the potentially infinite state of the blockchain. The Ethereum blockchain is currently tens of gigabytes, but the current state of the blockchain, as of this recording, is this hexadecimal hash representing 256 bits.
What about digital signatures? Digital signatures, like real signatures, are a way to prove that somebody is who they say they are, except that we use cryptography or math, which is more secure than handwritten signatures that can be easily forged. A digital signature is a way to prove that a message originates from a specific person and no one else, like a hacker.
Digital signatures are used today all over the Internet. Whenever you visit a website over ACTPS, you are using SSL, which uses digital signatures to establish trust between you and the server. This means that when you visit Facebook.com, your browser can check the digital signature that came with the web page to verify that it indeed originated from Facebook and not some hacker.
In asymmetric encryption systems, users generate something called a key pair, which is a public key and a private key using some known algorithm. The public key and private key are associated with each other through some mathematical relationship. The public key is meant to be distributed publicly to serve as an address to receive messages from other users, like an IP address or home address. The private key is meant to be kept secret and is used to digitally sign messages sent to other users. The signature is included in the message so that the recipient can verify using the sender’s public key. This way, the recipient can be sure that only the sender could have sent this message. Generating a key pair is analogous to creating an account on the blockchain, but without having to actually register anywhere. Pretty cool. Also, every transaction that is executed on the blockchain is digitally signed by the sender using their private key. This signature ensures that only the owner of the account can move money out of the account.
To bring it all together, blockchain could not exist without hashing and digital signatures. Hashing provides a way for everyone on the blockchain to agree on the current world state, while digital signatures provide a way to ensure that all transactions are only made by the rightful owners. We rely on these two properties to ensure that the blockchain has not been corrupted or compromised.
If you want to take a deeper dive into hashing and digital signatures, check out our online courses.






masters dissertation writing services uk https://mydissertationwritinghelp.com/
dissertation writing software https://help-with-dissertations.com/
writing dissertation literature review https://dissertationwriting-service.com/
dissertation help sites https://buydissertationhelp.com/
online free slots https://slotmachinegameinfo.com/
free 777 slots no download https://www-slotmachines.com/
sexy girl slots https://411slotmachine.com/
fa fa fa slots https://download-slot-machines.com/
computer memory slots https://beat-slot-machines.com/
459 free casino slots https://slot-machine-sale.com/
free slots to play now https://slotmachinesforum.net/
cleopatra slots free https://slotmachinesworld.com/
konami slots https://pennyslotmachines.org/
cash me out slots youtube https://candylandslotmachine.com/
ff tactics 24 slots https://freeonlneslotmachine.com/
cleopatra slots https://2-free-slots.com/
gay seniors dating https://speedgaydate.com/
gay video chat private show https://gaytgpost.com/
which of the following statements about dating in gay male and lesbian youth is true? https://gaypridee.com/
dubuque gay chat https://bjsgaychatroom.info/
3rousing
9Soft Solution is a social media advertising platform that can assist you in gaining access to your social networking sites. We are a digital creative agency that helps people improve their
lives by working together to succeed in life and company DIGITAL CREATIVE AGANCY
I am curious in the statement “Digital signatures are used today all over the Internet. Whenever you visit a website over ACTPS, you are using SSL,” is that HTTPS? or what is ACTPS?
I am curious in the statement “Digital signatures are used today all over the Internet. Whenever you visit a website over ACTPS, you are using SSL,” is that HTTPS? or what is ACTPS?
I am curious in the statement “Digital signatures are used today all over the Internet. Whenever you visit a website over ACTPS, you are using SSL,” is that HTTPS? or what is ACTPS?
yeah excellent article
yeah excellent article
yeah excellent article
Excellent explanation about the new technology, which is disrupting the many industries and becoming the transformative part of our life.
Excellent explanation about the new technology, which is disrupting the many industries and becoming the transformative part of our life.
Excellent explanation about the new technology, which is disrupting the many industries and becoming the transformative part of our life.
Another superb video and tutorial: congratulations and thank you for sharing!
Another superb video and tutorial: congratulations and thank you for sharing!
Another superb video and tutorial: congratulations and thank you for sharing!
Haseeb you’re killing it. Love this article.
Haseeb you’re killing it. Love this article.
Haseeb you’re killing it. Love this article.