Contents
|
|
We have seen many high profile cryptocurrency hacks over the past few years. In this guide, we are going to be talking about, in our opinion, the five most important hacks that shook the crypto-world down to its very core. The intention is not to scare you, but to educate you and make you understand why these attacks happened. If you are interested in learning more about how cryptocurriences work in detail, please take a look at our dedicated blockchain courses.
Contents
5 High Profile Cryptocurrency Hacks
The Mt.Gox Hack
The year is 2013 and Max Karpeles is on the top of the world.

His Japan-based company Mt. Gox (Magic The Gathering Online Exchange) was by far the biggest bitcoin exchange in the world. It was the world’s largest bitcoin intermediary handling 70% of the world’s bitcoin exchanges. Things were looking good for Karpeles and he was working on many interesting concepts like the Bitcoin Café. However, there were cracks emerging underneath the surface.
The Problems with Mt. Gox
There were many problems with Mt Gox before the 2014 hack even happened and all that could be traced back to highly incompetent management. In many ways, it was a disaster waiting to happen. A Tokyo based software developer, who had visited the company looking for employment opportunities was appalled by what he saw.
Problem #1: Lack of A VCS
Firstly, there was a lack of a Version Control Software (VCS). A VCS is a must have in any software development company for a variety of reasons.
- A VCS enables you to keep track of all the changes made in the codebase. Using VCS, not only helps one to see precisely at what time the code was changed, it also helps them know who did it. It also allows one to rollback the change and goes back to the previous version.
- Another great quality of VCS is that it helps a lot of people code together at the same time without the fear of one programmer overlapping another’s code. This could have been really helpful in a company like Mt. Gox which has multiple programmers working on the same code at the same time.
Problem #2: Lack of A Testing Policy
The software developer also came across another highly-alarming piece of news. Until recently, Mt. Gox didn’t have a testing policy. Think about that for a moment. The biggest bitcoin exchange platform in the world didn’t have a testing policy! They were literally throwing out an untested code to their customers! And it gets even worse.
Problem #3: Bottleneck Issue
Turns out, Mt. Gox had a bottleneck issue. All the changes in the code had to be approved by the Ceo himself. Karpeles was the end all and be all of the whole system. That’s just bad management (more on this later). The CEO of the company should never be a bottleneck of the whole coding process but that is what exactly happened.
Problem #4: Lack of Proper Management
If we were to surmise all the issues, it all comes down to one thing. Highly Incompetent and childish management. Andreas Antonopoulos, in a very scathing report, had this to say:
“Magic The Gathering Online Exchange is a systemic risk to bitcoin, a death trap for traders and a business run by the clueless.”
Those are some very harsh words, but there is so much truth in that statement. The thing is that Karpeles was more of an idealistic programmer than a businessman. While he could code, he could never have the acumen needed to run a company. And, unfortunately, because of this, a huge disaster was incoming. But it is not like nobody didn’t see it coming.
The 2011 Hack: A Sign of Things to Come
On June 19, 2011, a strange thing happened. The value of bitcoin in Mt. Gox fell all the way down to one cent!
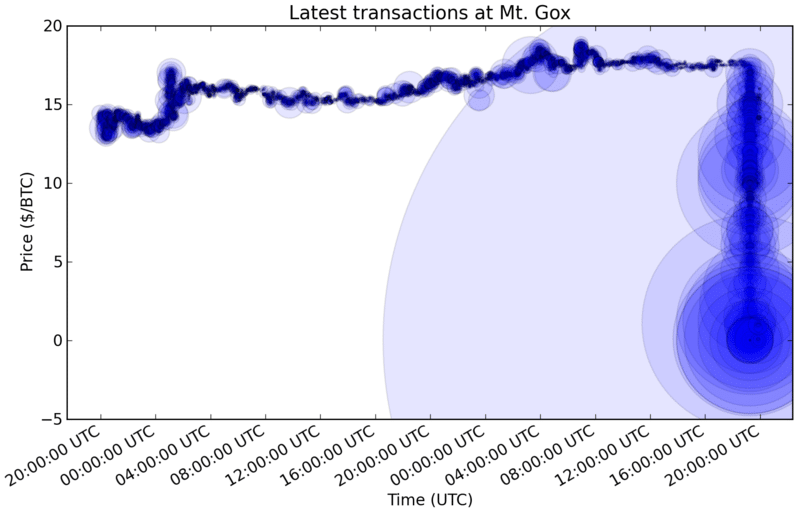
Image Courtesy: Wikipedia
See that image above?
That’s a graph of all the Bitcoin transactions made on Mt.Gox Bitcoin Exchange on 19 June 2011, showing the price crash. The size of circular plot denotes the size of a transaction.
So, what exactly happened and why did the price go down?
The attacker hacked into a Mt. Gox auditor’s computer and used it to transfer a huge amount of bitcoins to themselves. They used the exchange’s software to sell all these bitcoins and this created a huge strain on the system as a result of which the value of the bitcoins in the system dropped dramatically.
Even though the price was re-adjusted in a few mins a lot of damage was already done. Accounts with the equivalent of more than $8,750,000 were affected. While Mt. Gox did manage to crawl back from this disaster, nothing could save them from the catastrophe that was about to come.
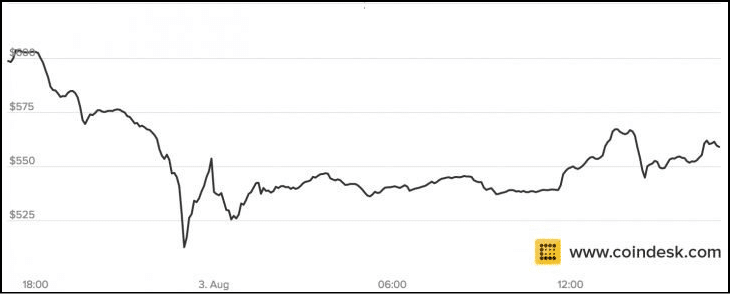
The 2014 Hack: The $473 Million Robbery
Going into 2014 Mt. Gox users were complaining about long delays in service. In fact, it got so bad that the US banking system actually froze Mt. Gox out because of the regulatory problems. On 7th February 2014, the company stopped all bitcoin withdrawals to look through the technical processes in the company and see why the delays were happening.
They released the following statement:
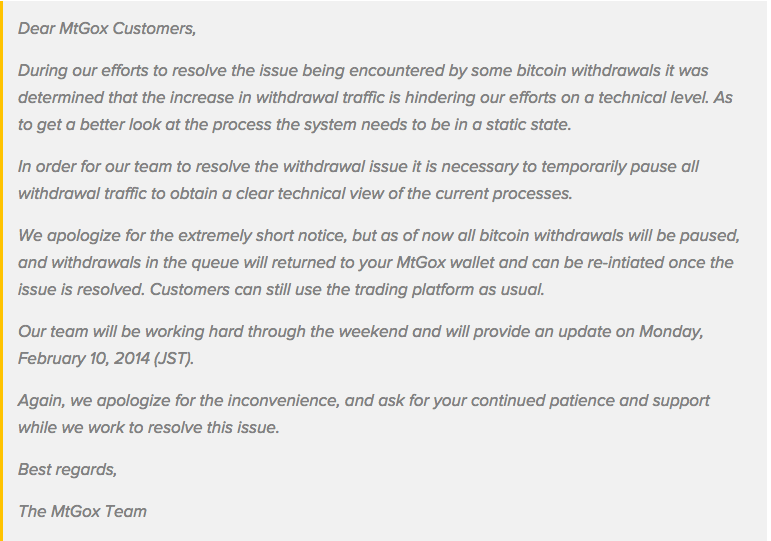
Image Courtesy: Coindesk
During their check, they realized that they had been subjected to a transaction malleability attack.
What is Transaction Malleability?
Before we understand that, let’s check a look at what a simple transaction code in bitcoin looks like.
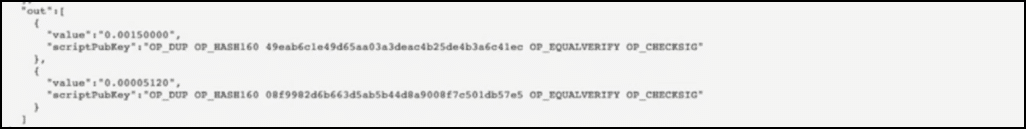
This is what the transaction looks like in the code form. Suppose Alice wants to send 0.0015 BTC to Bob and in order to do so, she sends inputs which are worth 0.0015770 BTC. This is what the transaction detail looks like:
Image courtesy: djp3 youtube channel.
The first thing that you see:
Is the name of the Transaction aka the hash of the input and output value.
Vin_sz is the number of input data, since Alice is sending the data using only one of her previous transactions, it is 1.
Vout_sz is 2 because the only outputs are Bob and the change that Alice will get back.
This is the Input data:
Alice is only using one input transaction, this is the reason why vin_sz was 1.
Below the input data is her signature data (this is important to remember it as we go forward).
Underneath all this is the output data:
The first part of the data signifies that Bob is getting 0.0015 BTC.
The second part signifies that 0.00005120 BTC is what Alice is getting back as change.
Now, remember that our input data was 0.0015770 BTC? This is greater than (0.0015 + 0.00005120). The deficit of these two values is the transaction fee that the miners are collecting.
So, this is the anatomy of a simple transaction.
Now there is one more thing that you need to know before we understand what transaction malleability can do. The blockchain was created to be completely immutable, which it achieves through cryptographic hash functions. What this essentially means is that once data has been put inside the blockchain you cannot tamper with it. Just this quality alone gives blockchain based cryptocurrencies immense security.
However, there is a loophole
What if the data tampering happens before you put the data in the blockchain? Even if the tampering gets noticed, nobody can do anything about it once it goes inside the blockchain.
This is called Transactional Malleability.
So how can you tamper with the data?
Remember we told you to keep in mind the signature data during the input?
Turns out that the signature that goes along with the input data can be manipulated, which in turn can change the transaction ID. In fact, it can make it seem like the transaction didn’t even happen in the first place. Let’s see this in an example.
Suppose Bob wants Alice to send him 3 BTC. Alice initiates a 3 BTC transaction to Bob’s public address and then sends it over to the miners for approval. While the transaction is waiting in the queue, Bob uses transaction malleability to alter Alice’s signature and change the transaction ID.
Now there is a chance that this tampered transaction will be approved before Alice’s gets approved, which in turn overwrites Alice’s transaction. When Bob gets his 3 BTC, he can simply tell Alice that he didn’t get the 3 BTC that she owed him. Alice will then see that her transaction didn’t go through and will them resend it. As a result, Bob will end up with 6 BTC instead of 3 BTC.
And that is exactly what is said to have happened during the Mt. Gox hack. Because of extreme mismanagement and a lack of a contingency plan, around $473 million worth of bitcoins, which was around 7% of the world’s supply of bitcoins, were stolen from the system.
The Aftermath
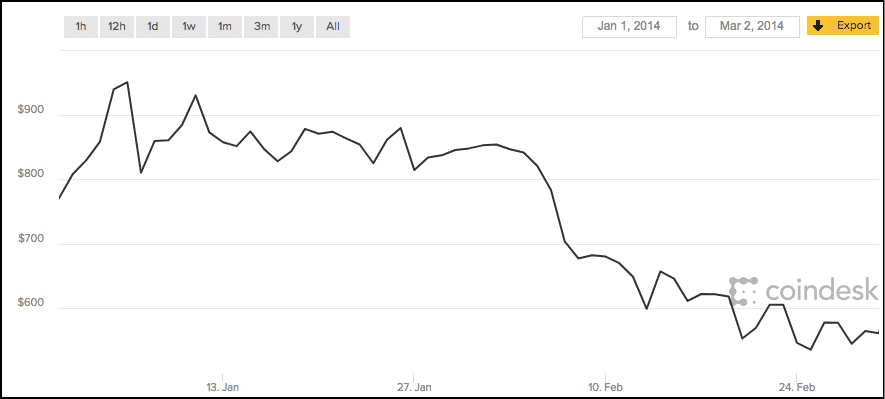
The timing of the Mt. Gox attack was very unfortunate. This was at the time that Bitcoin was slowly getting mainstream exposure. It was feared that the Mt. Gox attack could put back faith in the system by at least 4-5 years. The immediate signs were disturbing as well. The value of BTC fell drastically as is evident from the graph below:
Image Courtesy: Coindesk
Mt. Gox declared bankruptcy and it was later discovered that the money stolen was being laundered through another exchange called BTC-e. The owner of BTC-e, Alexander Vinnik was arrested in Greece. He is being accused of laundering the money that he obtained through Mt. Gox through BTC-e and Tradehill, another exchange that he happens to own. The Greek court has cleared his extradition to the US where he faces up to 55 years in prison if accused.
Bitcoin has thankfully gotten past this incident and has been growing from strength to strength ever since.
The DAO Hack
So, moving on from the biggest attack that rocked Bitcoin, to the biggest attack that Ethereum has faced till date. The attack and its aftermath were so severe that the developers were forced to create a whole new currency to deal with the repercussions! So, before we understand what the DAO attack was, let’s give us a little history lesson.
The Formation of The DAO
The entire ecosystem of Ethereum works on the basis of smart contracts. For the uninitiated, smart contracts are basically how things get done in the Ethereum eco-system. To put it in layman terms, smart contracts are automated contracts that enforce and facilitate the terms of the contract itself.
The DAO aka the Decentralized Autonomous Organization was a complex smart contract which was going to revolutionize Ethereum forever. It was basically going to be a decentralized venture capital fund which was going to fund all future DAPPS made in the eco-system.
The way it worked was pretty straightforward. If you wanted to have any say in the direction DAPPS that would get funded, then you would have to buy “DAO Tokens” for a certain amount of Ether. The DAO tokens were indicators that you are now officially part of the DAO system.
So, how was DAPPS going to get approved and built? Well, firstly they need to get whitelisted by the curators, who have basically known figureheads in the Ethereum world. After getting their stamp of approval they will get voted on by the DAO token holders. If the proposal gets a 20% approval in the vote, then they will get the required funds to get started.
The potential of the DAO and the flexibility, control and complete transparency that it offered was unprecedented, people leaped in to get their share of the pie. Within 28 days of its formation, it accumulated over $150 million worth of ether in a crowdsale. At that time, it had 14% of all ether tokens issued to date.
You might be wondering, that’s all good but how does one go out of the DAO? What if some DAPP gets approved that you are not a huge fan of, how do you opt out of the DAO then? To enable this, an exit door was created called the “Split Function”. Using this function, you would get back the ether you have invested and, if you so desired, you could even create your own “Child DAO”. In fact, you could split off with multiple DAO token holders and create your own Child DAO and start accepting proposals.
There was one condition in the contract, however, after splitting off from the DAO you would have to hold on to your ether for 28 days before you could spend them. So everything looks nice and spiffy for now….except, there was one little problem. A lot of people saw this possible loophole and pointed it out. The DAO creators assured that this was not going to be a big issue. The only thing is, it was and that created the entire storm that split Ethereum into Ethereum and Ethereum Classic.
The DAO Attack
On 17th June 2016, someone exploited this very loophole in the DAO and siphoned away one-third of the DAO’s funds. That’s around $50 million dollars. The loophole that the hacker(s) discovered was pretty straightforward in the hindsight.
If one wished to exit the DAO then they can do so by sending in a request. The splitting function will then follow the following two steps:
- Give the user back his/her Ether in exchange for their DAO tokens.
- Register the transaction in the ledger and update the internal token balance.
What the hacker did was they made a recursive function in the request, so this is how the splitting function went:
- Take the DAO tokens from the user and give them the Ether requested.
- Before they could register the transaction, the recursive function made the code go back and transfer even more Ether for the same DAO tokens.
This went on and on until $50 million worth of Ether were taken out and stored in a Child DAO and as you would expect, pandemonium went through the entire Ethereum community.
Note: Before we continue with the article let’s make one distinction clear. The hack happened because of an issue in the DAO not because of any issues in the Ethereum itself. Ethereum runs in the background while DAO runs on it.
As Gavin Wood, the co-founder of Ethereum puts it, blaming Ethereum for the DAO hack is like saying “The Internet is broken” every time a website goes down.
The Aftermath
The Ethereum community got together and decided that a soft fork was the best way to go forward. Not only is a soft fork backwards compatible, it would have made the “Dao Attack” disappear. However, during implementation, the developers realized that a soft-fork would result in a lot of DDOS (Denial of Service) attacks. The only other option was to hard fork the chain and this split up the community. This “split” resulted in two different Ethereums. The original Ethereum Classic (ETC) and the new post hard-fork coin Ethereum (ETH).
The Bitfinex Hack

Image courtesy: AltCoin Today
The second biggest in the history of bitcoin was suffered by Hong Kong-based cryptocurrency exchange platform, Bitfinex. 120,000 BTC which was worth $72 million back then was stolen. Bitfinex announced the hack on August 2, 2016. Before we understand how and why the hack happened, we need to refresh some concepts first.
What is a multi-sig wallet?
Image Courtesy: Coin Hako blog
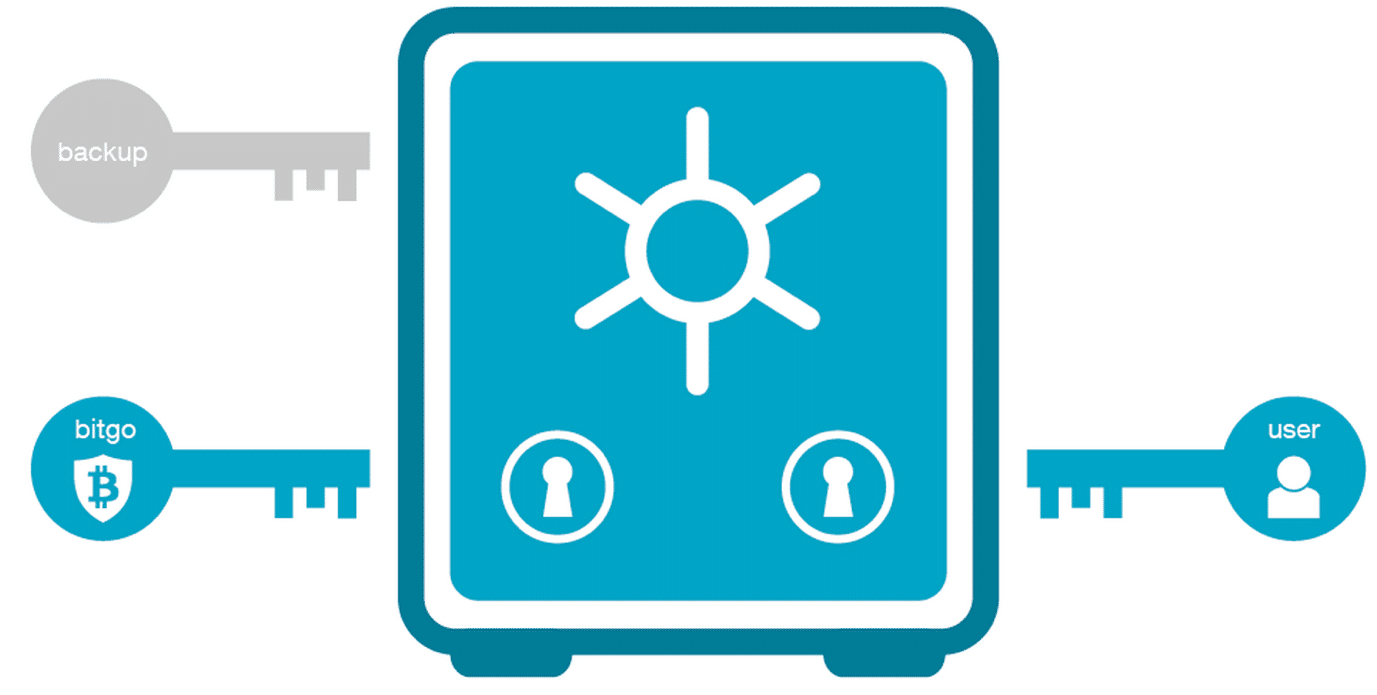
The easiest way of understanding how a multi-signature (multi-sig) wallet works like is by thinking of a safe which needs multiple keys to operate. A multi-signature wallet is great for 2 purposes:
- To create more security for your wallet and save yourself from human error.
- To create a more democratic wallet which can be used by one or more people.
How does multi-signature wallet save you from human error? Let’s take the example of BitGo, one of the premier multi-sig wallet service providers in the world. They issue 3 private keys. One is held by the company itself, one is held by the user and the third one is a backup that the user can keep for themselves or give to someone trustworthy for safekeeping To do any sort of transaction in a BitGo wallet you will need at least 2/3 keys to operate. So even if you have a hacker behind you, it will super difficult for them to get their hands on 2 private keys. And on top of that, even if you lose your private key for whatever reason, you still have that backup key that you had given to your friend.
Now, how does a multi-signature wallet create a more democratic environment? Imagine that you are working in a company with 10 people and you need 8 approvals in order to make a transaction. Using a software like Electrum you can simply create a custom multi-sig wallet with 10 keys. This way you can make seamless democratic transactions in your company.
Even with all its amazing features, at the end of the day, a multi-signature wallet is still a hot wallet so you must use it economically. The Bitfinex hack (more on it in a bit) happened despite the fact that it had multi-signature security. Plus, at the end of the day, the company whose wallet you are using still has one of the private keys. It completely depends on their ethics as to what they can do or not do to your funds.
How did the hack happen?
The source of the problem was Bitfinex’s need to find a system which would give their users better security and liquidity options. Most of the exchanges are simple “hot” wallets which meant that they are always vulnerable to getting hacked. Bitfinex made a partnership with BitGo in 2015 and created a system whereby multi-signature wallets, those where keys are divided among a number of owners to manage risk, would be provided to each customer.
Bitfinex declared the following:
“The era of commingling customer bitcoin and all of the associated security exposures is over.”
However, ironical as it may seem, this “security measure” was what led to the hack. As discussed earlier, a multisignature wallet has keys divided among a number of owners to manage risk. In order for a transaction to go through, all parties need to sign off on it. In the case of Bitfinex, 2 keys would be stored by them while one will be stored by BitGo.
So, BitGo is supposed to act as an additional security and verify the validity of the transactions leaving Bitfinex. Because of this extra layer of security, Bitfinex reduced the use of cold storage wallets and stored their customer’s money in multisig hot wallets. The idea was to increase the ease of liquidity without compromising on the security. However, when the hackers attacked the Bitfinex servers, they managed to not only get Bitfinex to sign off on illegal bitcoin withdrawals, they sometimes circumvented BitGo’s security measures and got them to sign off on the withdrawals too!
There are a lot of theories as to why exactly that happened. Theories that go from conspiratorial to downright ridiculous. However, the most credible theory is that the system Bitfinex setup was broken such that BitGo would do whatever Bitfinex said to do with a user’s funds. So basically, the multi-sig wallets weren’t really multi-sig at all, there was only one point of failure and that was Bitfinex’s servers. Further weight is given to that theory when you keep in mind that BitGo has publicly declared that their servers weren’t the one that were compromised.
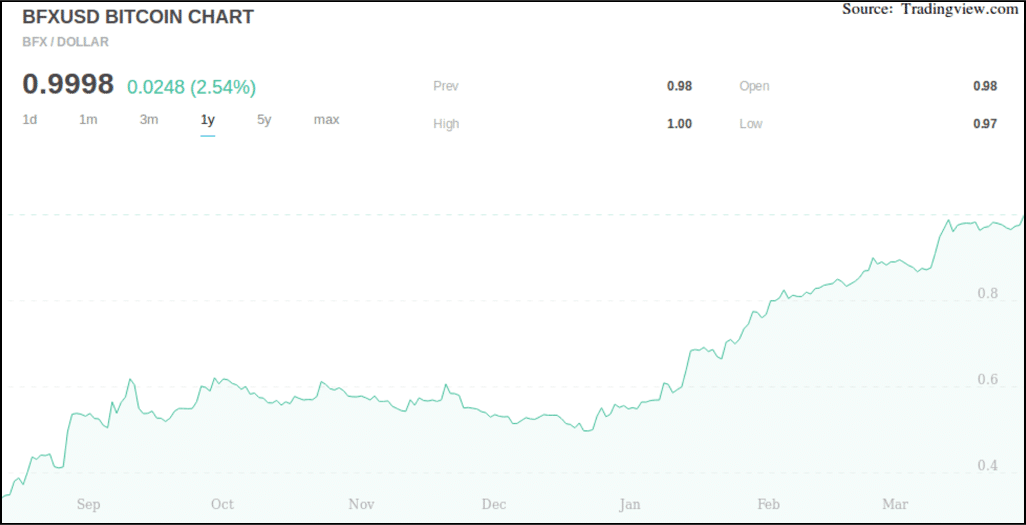
The Aftermath
The price of Bitcoin went into a tumble and fell nearly 20%. One BTC went as low as $480 before it managed to recover.
Image Courtesy: CoinDesk
While Bitfinex did take a hit, the way they redeemed themselves is certainly commendable.
They first issued a BFX token to all their customers, which was basically an IOU for all the funds that they owned them. However, rumors started circulating that this was just a scam from Bitfinex to buy more time to pay back the debt. On September 1, in order the allay the fears and doubts of the Bitcoin community, they bought back the first 1.1% of the tokens outstanding.
But that was not the end of their efforts. Bitfinex added more trading pairs, enabled faster withdrawals and created an OTC trading desk for larger trades and, eventually, business picked up enough to enable them to get out of debt faster.
Image Courtesy: Bitcoin.com
On April 3rd, 2017, Bitfinex stopped all trading of their BFX tokens and started allowing users to cash them out for their full value of $1 per BFX token.
The following table shows the full “BFX Token Redemption History”:
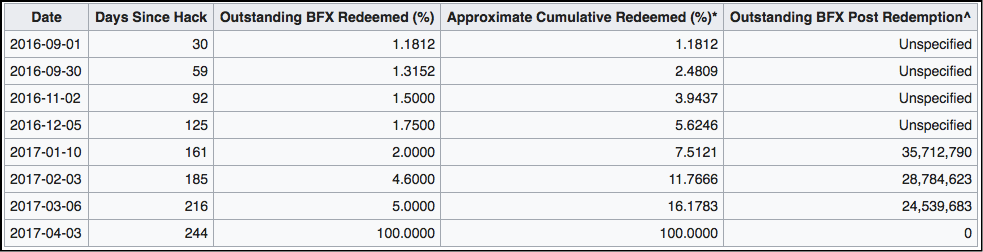
Image Courtesy: Wikipedia
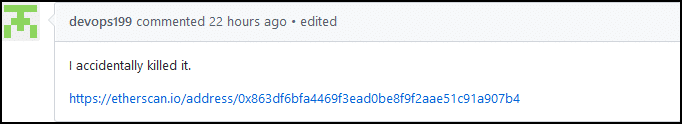
The Parity Multi-Sig Frozen Funds
While not technically a malicious hack, what has recently (as of writing), happened with the parity multi-sig wallets deserves a mention. Before we continue, huge shoutout to SpringRole for all the data. So, how often has it happened that you accidentally froze up to $150 million? That is exactly what happened to user “devops199” when he accidentally killed the contract: 0x863df6bfa4469f3ead0be8f9f2aae51c91a907b4.
Image Courtesy: SpringRole Medium
Little did he know that he just opened up Pandora’s Box.
On 20th of July, a new version of the Parity wallet contract was initiated because of a breach that happened before that. Unfortunately, there was a big flaw in this new code. It turns out that it was possible to turn the Parity Wallet library contract into a regular multi-sig wallet and become an owner of it by calling the initWallet function.
This is what the vulnerable piece of code looks like.
Parity employed library driven smart contract development for their multi-sig wallets. Meaning, all multi-sig wallets referenced this single library contract for all their functionality. In essence, all Partiy Mulit-Sig wallets had a single point of failure and that address was in the wallet library solidity code:
constant _walletLibrary = 0x863df6bfa4469f3ead0be8f9f2aae51c91a907b4
According to Reddit user, the ironically named, “ItsAConspiracy”, the reason why this design was done was to save up on gas cost. Instead of copying and pasting the same code in each and every unique multi-sig wallet, they started using a library which acts as a “common space” for all these wallets to delegate certain function calls too.
So basically, instead of having the same code repeated redundantly in every wallet, there was one common place where every wallet can do a call to get some functionalities done. This was done to save up on gas and storage space.
However, there was a fatal flaw as was unwittingly exploited by the user.
The user was basically able to initialize the library itself as a wallet, claiming owner rights for it, including the right to kill it altogether.
Every solidity contract has a “kill” function. Here is a sample kill function to give you an idea:
function kill()
{
if (msg.sender == creator)
{
suicide(creator);
}
}
The kill function exists to finish the contract and to hand over whatever tokens are left back to the contract creator.
It basically finishes a contract.
So, when the user killed the wallet, they basically killed the library and all the logic functions associated with it. That means, all the wallets that were linked to the library have become useless and ~$150 mil has been frozen up.
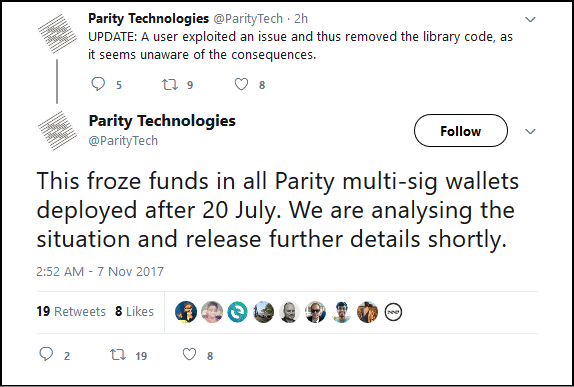
The Aftermath
This is what Parity had to say about the whole fiasco:
Image Courtesy: SpringRole Medium
As of writing the funds are still locked up.
Since Ethereum is immutable, this action can’t be undone. The only way that the funds can be brought back is via a hardfork.
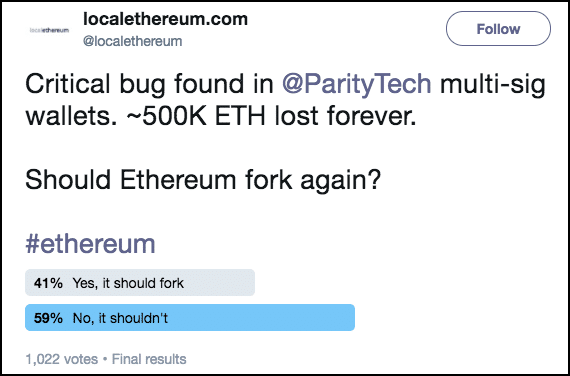
The Ethereum community is extremely divisive about this, a lot of twitter polls are showing nearly 50-50 support and dissent for the “hardfork solution”. Here is an example of such a poll:
As of right now, $150 million worth of Ether is just floating around with no one to stake their claim to it.
Bonus: NiceHash Hack
On December 6th, 2017 at 00:18 GMT, Slovenian based mining company NiceHash was hacked for 4700 BTC which is ~$80 million.
Marko Kobal, the chief executive officer of NiceHash, appeared on Facebook Live to address concerns about the attack. He didn’t reveal much apart from saying that an employee’s computer was compromised during the attack which leads to the heist.
The attackers basically used the employee’s credentials to gain access to the NiceHash system. This is what Kobal had to say:
“Given the complexity and security of the systems in place, this appears as an incredibly coordinated and highly sophisticated attack.”
NiceHash suspended operations for 24 hours to do a thorough checkup and analysis of the hack.
This is what the company said in their press release statement:
“Importantly, our payment system was compromised and the contents of the NiceHash Bitcoin wallet have been stolen. We are working to verify the precise number of BTC taken. Clearly, this is a matter of deep concern and we are working hard to rectify the matter in the coming days. In addition to undertaking our own investigation, the incident has been reported to the relevant authorities and law enforcement and we are co-operating with them as a matter of urgency.”
Cryptocurrency Hacks Conclusion
So, there you have it. The four most important (in our opinion) crypto hacks which have happened in the last few years. While one was staggering because of the sheer scale of the robbery (Mt Gox) and the utterly ridiculous mismanagement that caused it, the other (DAO) was so severe that it created a new coin to compensate for the damage caused. And of course, we have the accidental catastrophe of the parity multi-sig fiasco.
However, the Bitfinex attack shows that no matter what is thrown at the crypto-world, they will always find a way to fight and bounce back.
That, in essence, is the purpose of this article. To educate you about the attacks, and to show you that no matter what happens, this crazy and amazing world of cryptocurrency always bounces back and comes back stronger. As with any monetary system, there are flaws, and all developer team should be focused on continued security testing with audits and penetration testing. However, one cannot deny the sheer will to survive and thrive as is very evident when you look at the crypto-world.








Some years ago I had a few misdemeanors and was wrongly convicted for prostitution when I was just turning 22, and bad friends got me into this situation. It makes it hard for me to get a job when employers background check me, at the same time i had a big issue with a bad guy that threatened to blackmail me. I was so so depressed with no hope at all until i found this hacker on Google after seeing different wonderful reviews about his services. He helped me clear criminal records, track down the fool that has been hacking into my personal stuff and stealing my bitcoin, also deleted some negative news about me online within 48 hours. I have actually found a special kind & reliable hacker so I am going to tell everybody about this for safety reasons. This is where you can reach him for any hacking related issue. [computerworm.hacker. . HOTMAIL com]
Very informative and educational for a green horn looking to become great in coding.
I think I identified a new line of action for us to break even, getting a solution to reversing what we code,
furthermore, we should add a reversal subscript to whatever we code to enable us reverse if need be and possibly lock with a VSC. (Don’t critique me much, thinking like a green horn you know) hahaha.
This paragraph from the Mt God hack confuses me a bit.
“The attacker hacked into a Mt. Gox auditor’s computer and used it to transfer a huge amount of bitcoins to themselves. They used the exchange’s software to sell all these bitcoins and this created a huge strain on the system as a result of which the value of the bitcoins in the system dropped dramatically.”
What about the sell off caused the system such strain that the price fell off so quickly. Was it that sales were not being verified quickly or was it that the hackers selling dropped the price ? And how did he manage selling all the bitcoin with no buyers ?
“Turns out that the signature that goes along with the input data can be manipulated, which in turn can change the transaction ID. In fact, it can make it seem like the transaction didn’t even happen in the first place. Let’s see this in an example.”
Absolutely unclear how this situation is possible, input signature is “hash” created by using transaction data + secret key. To steal money you have to change TO address which will destroy signature. I have a feeling that you don’t know how this hack worked, because your explanation and example gives me zero explanation. What part of transaction was changed ? Why a signature was valid after the change ? If signature was invalid how this transaction was added to a block, any miner should reject it. If you change a transaction you will change its hash it is clear but did it help hackers ? It looks that malleability hack is a myth, because I don’t see how it might work.
Is it Max Karpeles? I thought it was was Mark
very educating, was scared reading but reassuring with the knowledge you provide
thank You
very educating, was scared reading but reassuring with the knowlegde you provide
thank You